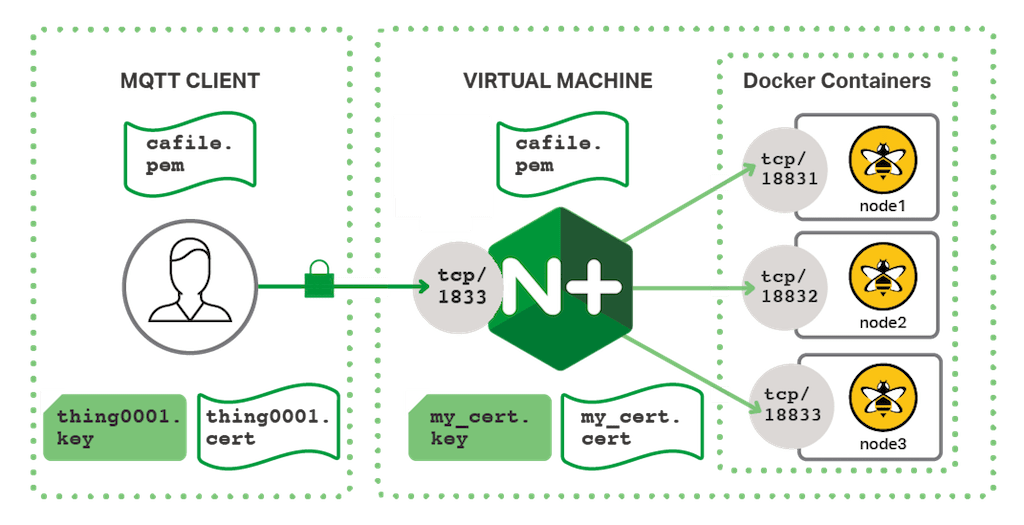
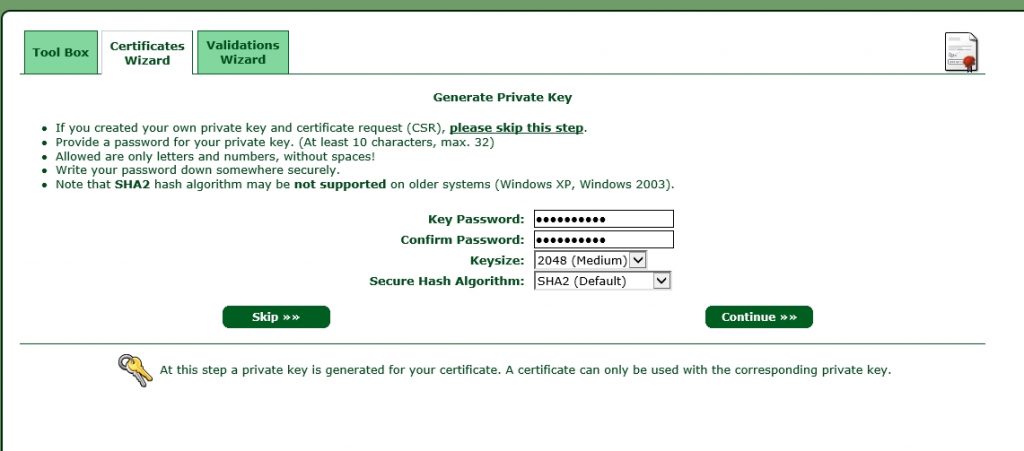
This article provides a guide on how to generate your own TLS certificates and keys for OpenVPN connection that uses TLS authentication. This guide is aimed at Ubuntu users. Step 1: downloading Easy-Rsa edit edit source Almost all of the steps will be done through the terminal. Mar 29, 2020 How To Create A Free TLS Certificate. Here we take a look at the step by step procedure to create a free TLS certificate. Get a domain, DNS, and hosting. Before even thinking of getting a TLS certificate, you must have a domain you want to use it for. This article provides a guide on how to generate your own TLS certificates and keys for OpenVPN connection that uses TLS authentication. This guide is aimed at Ubuntu users. Step 1: downloading Easy-Rsa edit edit source Almost all of the steps will be done through the terminal. Oct 07, 2019 To generate an SSL certificate and CSR, perform the following steps: In the Domains text box, enter the domain name of the website that the certificate will secure. You can enter a wildcard-formatted domain name to install the same certificate on any number of subdomains if they share an IP address. In the previous article, we’ve talked about how digital certificates help with authentication and provide a safe and reliable key exchange process in TLS. Today we will learn exactly how to generate a certificate and have it signed by a Certificate Authority (CA).
-->An ingress controller is a piece of software that provides reverse proxy, configurable traffic routing, and TLS termination for Kubernetes services. Kubernetes ingress resources are used to configure the ingress rules and routes for individual Kubernetes services. Using an ingress controller and ingress rules, a single IP address can be used to route traffic to multiple services in a Kubernetes cluster.
This article shows you how to deploy the NGINX ingress controller in an Azure Kubernetes Service (AKS) cluster. You generate your own certificates, and create a Kubernetes secret for use with the ingress route. Finally, two applications are run in the AKS cluster, each of which is accessible over a single IP address.
You can also:
- Create an ingress controller that uses Let's Encrypt to automatically generate TLS certificates with a dynamic public IP address or with a static public IP address
Before you begin
This article uses Helm to install the NGINX ingress controller and a sample web app. You need to have Helm initialized within your AKS cluster and using a service account for Tiller. Make sure that you are using the latest release of Helm. For upgrade instructions, see the Helm install docs. For more information on configuring and using Helm, see Install applications with Helm in Azure Kubernetes Service (AKS).
This article also requires that you are running the Azure CLI version 2.0.64 or later. Run az --version to find the version. If you need to install or upgrade, see Install Azure CLI.
Create an ingress controller
To create the ingress controller, use Helm to install nginx-ingress. For added redundancy, two replicas of the NGINX ingress controllers are deployed with the --set controller.replicaCount parameter. To fully benefit from running replicas of the ingress controller, make sure there's more than one node in your AKS cluster.
The ingress controller also needs to be scheduled on a Linux node. Windows Server nodes (currently in preview in AKS) shouldn't run the ingress controller. A node selector is specified using the --set nodeSelector parameter to tell the Kubernetes scheduler to run the NGINX ingress controller on a Linux-based node.
Tip
The following example creates a Kubernetes namespace for the ingress resources named ingress-basic. Specify a namespace for your own environment as needed. If your AKS cluster is not RBAC enabled, add --set rbac.create=false to the Helm commands.
Tip
If you would like to enable client source IP preservation for requests to containers in your cluster, add --set controller.service.externalTrafficPolicy=Local to the Helm install command. The client source IP is stored in the request header under X-Forwarded-For. When using an ingress controller with client source IP preservation enabled, SSL pass-through will not work.
During the installation, an Azure public IP address is created for the ingress controller. This public IP address is static for the life-span of the ingress controller. If you delete the ingress controller, the public IP address assignment is lost. If you then create an additional ingress controller, a new public IP address is assigned. If you wish to retain the use of the public IP address, you can instead create an ingress controller with a static public IP address.
To get the public IP address, use the kubectl get service command. It takes a few minutes for the IP address to be assigned to the service.
Make a note of this public IP address, as it's used in the last step to test the deployment.
No ingress rules have been created yet. If you browse to the public IP address, the NGINX ingress controller's default 404 page is displayed.
Generate TLS certificates
For this article, let's generate a self-signed certificate with openssl. For production use, you should request a trusted, signed certificate through a provider or your own certificate authority (CA). In the next step, you generate a Kubernetes Secret using the TLS certificate and private key generated by OpenSSL.
The following example generates a 2048-bit RSA X509 certificate valid for 365 days named aks-ingress-tls.crt. The private key file is named aks-ingress-tls.key. A Kubernetes TLS secret requires both of these files.
This article works with the demo.azure.com subject common name and doesn't need to be changed. For production use, specify your own organizational values for the -subj parameter:
Create Kubernetes secret for the TLS certificate
To allow Kubernetes to use the TLS certificate and private key for the ingress controller, you create and use a Secret. The secret is defined once, and uses the certificate and key file created in the previous step. You then reference this secret when you define ingress routes.
The following example creates a Secret name aks-ingress-tls:
Run demo applications
An ingress controller and a Secret with your certificate have been configured. Now let's run two demo applications in your AKS cluster. In this example, Helm is used to deploy two instances of a simple 'Hello world' application.
Before you can install the sample Helm charts, add the Azure samples repository to your Helm environment as follows:
Create the first demo application from a Helm chart with the following command:
Now install a second instance of the demo application. For the second instance, you specify a new title so that the two applications are visually distinct. You also specify a unique service name:
Create an ingress route
Both applications are now running on your Kubernetes cluster, however they're configured with a service of type ClusterIP. As such, the applications aren't accessible from the internet. To make them publicly available, create a Kubernetes ingress resource. The ingress resource configures the rules that route traffic to one of the two applications.
In the following example, traffic to the address https://demo.azure.com/ is routed to the service named aks-helloworld. Traffic to the address https://demo.azure.com/hello-world-two is routed to the ingress-demo service. For this article, you don't need to change those demo host names. For production use, provide the names specified as part of the certificate request and generation process.
Tip
If the host name specified during the certificate request process, the CN name, doesn't match the host defined in your ingress route, you ingress controller displays a Kubernetes Ingress Controller Fake Certificate warning. Make sure your certificate and ingress route host names match.
The tls section tells the ingress route to use the Secret named aks-ingress-tls for the host demo.azure.com. Again, for production use, specify your own host address.
Create a file named hello-world-ingress.yaml and copy in the following example YAML.
Create the ingress resource using the kubectl apply -f hello-world-ingress.yaml command.
Windows 7 is the most used operating system which is released in back July, 2009. If you have problem with your current running windows 7 in your system and want to repair or re install windows then you need have windows 7 product key or serial key.I give you trial product but once you are satisfied and you have enough money, I highly recommend you to buy windows 7 Home Premium product key to support the developers.To buy product key you visitI will provide you Windows 7 Home Premium Product Key, Windows 7 Home Premium 32 bit product key, Windows 7 Home Premium 64 bit key, windows 7 genuine. Product key generator windows 7.
Test the ingress configuration
To test the certificates with our fake demo.azure.com host, use curl and specify the --resolve parameter. This parameter lets you map the demo.azure.com name to the public IP address of your ingress controller. Specify the public IP address of your own ingress controller, as shown in the following example:
No additional path was provided with the address, so the ingress controller defaults to the / route. The first demo application is returned, as shown in the following condensed example output:
The -v parameter in our curl command outputs verbose information, including the TLS certificate received. Half-way through your curl output, you can verify that your own TLS certificate was used. The -k parameter continues loading the page even though we're using a self-signed certificate. The following example shows that the issuer: CN=demo.azure.com; O=aks-ingress-tls certificate was used:
Now add /hello-world-two path to the address, such as https://demo.azure.com/hello-world-two. The second demo application with the custom title is returned, as shown in the following condensed example output:
Clean up resources
This article used Helm to install the ingress components and sample apps. When you deploy a Helm chart, a number of Kubernetes resources are created. These resources include pods, deployments, and services. To clean up these resources, you can either delete the entire sample namespace, or the individual resources.
Delete the sample namespace and all resources
To delete the entire sample namespace, use the kubectl delete command and specify your namespace name. All the resources in the namespace are deleted.
Then, remove the Helm repo for the AKS hello world app:
Delete resources individually
Alternatively, a more granular approach is to delete the individual resources created. List the Helm releases with the helm list command. Look for charts named nginx-ingress and aks-helloworld, as shown in the following example output:
Delete the releases with the helm delete command. The following example deletes the NGINX ingress deployment and the two sample AKS hello world apps.
Next, remove the Helm repo for the AKS hello world app:
Remove the ingress route that directed traffic to the sample apps:
Delete the certificate Secret:
Finally, you can delete the itself namespace. Use the kubectl delete command and specify your namespace name:
Next steps
This article included some external components to AKS. To learn more about these components, see the following project pages:
Generate Tls Certificate Linux
You can also:
- Create an ingress controller that uses Let's Encrypt to automatically generate TLS certificates with a dynamic public IP address or with a static public IP address
Updated by LinodeWritten by Linode
Report an Issue View File Edit File
What is a Self-Signed TLS Certificate?
Self-signed TLS certificates are suitable for personal use or for applications that are used internally within an organization. If you intend to use your SSL certificate on a website, see our guide on enabling TLS for NGINX once you’ve completed the process outlined in this guide.
Generate Tls Certificate And Key Free
Create the Certificate
Change to the
rootuser and change to the directory in which you want to create the certificate and key pair. That location will vary depending on your needs. Here we’ll use/root/certs:Create the certificate:
You will be prompted to add identifying information about your website or organization to the certificate. Since a self-signed certificate won’t be used publicly, this information isn’t necessary. If this certificate will be passed on to a certificate authority for signing, the information needs to be as accurate as possible.
The following is a breakdown of the OpenSSL options used in this command. There are many other options available, but these will create a basic certificate which will be good for a year. For more information, see
man opensslin your terminal.-newkey rsa:4096: Create a 4096 bit RSA key for use with the certificate.RSA 2048is the default on more recent versions of OpenSSL but to be sure of the key size, you should specify it during creation.-x509: Create a self-signed certificate.-sha256: Generate the certificate request using 265-bit SHA (Secure Hash Algorithm).-days: Determines the length of time in days that the certificate is being issued for. For a self-signed certificate, this value can be increased as necessary.-nodes: Create a certificate that does not require a passphrase. If this option is excluded, you will be required to enter the passphrase in the console each time the application using it is restarted.
Here is an example of the output:
Restrict the key’s permissions so that only
rootcan access it:Back up your certificate and key to external storage. This is an important step. Do not skip it!
Join our Community
This guide is published under a CC BY-ND 4.0 license.