- Red Hat Generate Ssh Host Keys List
- Ssh Generate Key Ubuntu
- Red Hat Generate Ssh Host Keys Download
- Redhat Generate Ssh Key
Nov 02, 2018 How to manually copy SSH public keys to servers on Red Hat Enterprise Linux. We often use ssh-copy-id to copy ssh keys from our local Linux computers to RHEL servers in order to connect without typing in a password. This is not only for convenience; it enables you to script and automate tasks that involve remote machines.
Sep 06, 2019 Keys can also be distributed using Ansible modules. The opensshkeypair module uses ssh-keygen to generate keys and the authorizedkey module adds and removes SSH authorized keys for particular user accounts. SSH key pairs are only one way to automate authentication without passwords. Under standard security practices, every host should generate unique host keys for SSH authentication. This enables SSH verification of the host ID to prevent man-in-the-middle or other attacks before the connection is made. If the host ID changes between sessions, by default SSH generates a warning and refuses the connection. SSH keys offer a highly secure manner of logging into a server with SSH as against mere dependence on a password. While a password stands the risk of being finally cracked, SSH keys are rather impossible to decipher using brute force. To be able to use ssh, scp, or sftp to connect to the server from a client machine, generate an authorization key pair by following the steps below. Note that keys must be generated for each user separately. SiteGround uses key-based authentication for SSH. This has proven more secure over standard username/password authentication. More information on SSH keys can be found here. You can generate an SSH key pair directly in cPanel, or you can generate the keys yourself and just upload the public one in cPanel to use with your hosting account. Aug 25, 2019 The public key can be shared, while the private key needs to stay secure. SSH key pairs are used to authenticate clients to servers automatically. When you create an SSH key pair, there is no longer a need to enter a password to access a server. On the host machine’s terminal, use this command to create a key pair: ssh-keygen -t rsa.
-->With a secure shell (SSH) key pair, you can create virtual machines (VMs) in Azure that use SSH keys for authentication, eliminating the need for passwords to sign in. This article shows you how to quickly generate and use an SSH public-private key file pair for Linux VMs. You can complete these steps with the Azure Cloud Shell, a macOS or Linux host, the Windows Subsystem for Linux, and other tools that support OpenSSH.
Note
VMs created using SSH keys are by default configured with passwords disabled, which greatly increases the difficulty of brute-force guessing attacks.
For more background and examples, see Detailed steps to create SSH key pairs.
For additional ways to generate and use SSH keys on a Windows computer, see How to use SSH keys with Windows on Azure.
Supported SSH key formats
Azure currently supports SSH protocol 2 (SSH-2) RSA public-private key pairs with a minimum length of 2048 bits. Other key formats such as ED25519 and ECDSA are not supported.
Create an SSH key pair
Use the ssh-keygen command to generate SSH public and private key files. By default, these files are created in the ~/.ssh directory. You can specify a different location, and an optional password (passphrase) to access the private key file. If an SSH key pair with the same name exists in the given location, those files are overwritten.
The following command creates an SSH key pair using RSA encryption and a bit length of 4096:
If you use the Azure CLI to create your VM with the az vm create command, you can optionally generate SSH public and private key files using the --generate-ssh-keys option. The key files are stored in the ~/.ssh directory unless specified otherwise with the --ssh-dest-key-path option. The --generate-ssh-keys option will not overwrite existing key files, instead returning an error. In the following command, replace VMname and RGname with your own values:
Provide an SSH public key when deploying a VM
To create a Linux VM that uses SSH keys for authentication, specify your SSH public key when creating the VM using the Azure portal, Azure CLI, Azure Resource Manager templates, or other methods:
If you're not familiar with the format of an SSH public key, you can display your public key with the following cat command, replacing ~/.ssh/id_rsa.pub with the path and filename of your own public key file if needed:
A typical public key value looks like this example:
If you copy and paste the contents of the public key file to use in the Azure portal or a Resource Manager template, make sure you don't copy any trailing whitespace. To copy a public key in macOS, you can pipe the public key file to pbcopy. Similarly in Linux, you can pipe the public key file to programs such as xclip.
The public key that you place on your Linux VM in Azure is by default stored in ~/.ssh/id_rsa.pub, unless you specified a different location when you created the key pair. To use the Azure CLI 2.0 to create your VM with an existing public key, specify the value and optionally the location of this public key using the az vm create command with the --ssh-key-values option. In the following command, replace VMname, RGname, and keyFile with your own values:
If you want to use multiple SSH keys with your VM, you can enter them in a space-separated list, like this --ssh-key-values sshkey-desktop.pub sshkey-laptop.pub.
SSH into your VM
With the public key deployed on your Azure VM, and the private key on your local system, SSH into your VM using the IP address or DNS name of your VM. In the following command, replace azureuser and myvm.westus.cloudapp.azure.com with the administrator user name and the fully qualified domain name (or IP address):
If you specified a passphrase when you created your key pair, enter that passphrase when prompted during the login process. The VM is added to your ~/.ssh/known_hosts file, and you won't be asked to connect again until either the public key on your Azure VM changes or the server name is removed from ~/.ssh/known_hosts.
If the VM is using the just-in-time access policy, you need to request access before you can connect to the VM. For more information about the just-in-time policy, see Manage virtual machine access using the just in time policy.
Don’t forget to read instructions after installation. Enjoy Trials Rising cd key working keygen serial key generator licence. All files are uploaded by users like you, we can’t guarantee that Trials Rising cd key working keygen serial key generator licence are up to date. Trials Rising License Activation Key generator! Trials Rising Keygen is here and it is FREE and 100% working and legit. – Trials Rising Serial Key Generator is an unique key code generator – This tool is able to generate a bunch of Trials Rising Keys – (NEW) CORE + Improved platform – The tool was meant for everyone, so it’s can be handled by any of you – This keygen can generate multiple key codes on a single IP. Click Bellow Button For Download Trials Rising Serial Key. When ever you accessed Trials Rising Generator, You have to select which plat of your stuff want to acquire generate a Redeem code. You can pick from Xbox One and PS4 games as being a Trials Rising Platform. Next press the Generate Redeem Code button and this will generate a Trials Rising. Trials rising activation key generator bus simulator 18 pc. May 03, 2019 TRIALS RISING KEY GENERATOR FOR FULL GAME Without doubt you’ll be able to generate cd keys what number you need. This Trials Rising Serial Keygen is without a doubt performing great and it is invisible by defense systems. Basically run that Trials Rising keygen and then wait around a moment and also have fun in video game.
Red Hat Generate Ssh Host Keys List
Next steps
For more information on working with SSH key pairs, see Detailed steps to create and manage SSH key pairs.
If you have difficulties with SSH connections to Azure VMs, see Troubleshoot SSH connections to an Azure Linux VM.
SSH (Secure SHELL) is an open source and most trusted network protocol that is used to login into remote servers for execution of commands and programs. It is also used to transfer files from one computer to another computer over the network using secure copy (SCP) Protocol.
In this article we will show you how to setup password-less login on RHEL/CentOS 7.x/6.x/5.x and Fedora using ssh keys to connect to remote Linux servers without entering password. Using Password-less login with SSH keys will increase the trust between two Linux servers for easy file synchronization or transfer.
My Setup Environment
If you are dealing with number of Linux remote servers, then SSH Password-less login is one of the best way to automate tasks such as automatic backups with scripts, synchronization files using scp and remote command execution.
In this example we will setup SSH password-less automatic login from server 192.168.0.12 as user tecmint to 192.168.0.11 with user sheena.
Step 1: Create Authentication SSH-Kegen Keys on – (192.168.0.12)
First login into server 192.168.0.12 with user tecmint and generate a pair of public keys using following command.
Create SSH RSA Key
Step 2: Create .ssh Directory on – 192.168.0.11
Use SSH from server 192.168.0.12 to connect server 192.168.0.11 using sheena as user and create .ssh directory under it, using following command.
Ssh Generate Key Ubuntu
Step 3: Upload Generated Public Keys to – 192.168.0.11
Use SSH from server 192.168.0.12 and upload new generated public key (id_rsa.pub) on server 192.168.0.11 under sheena‘s .ssh directory as a file name authorized_keys.
This should be your intention too, as a user, to fully evaluate Adobe Photoshop Lightroom CC 2015 6.1 withoutrestrictions and then decide.If you are keeping the software and want to use it longer than its trial time, we strongly encourage you purchasing the license keyfrom Adobe official website. Lightroom 5.3 serial key generator.
Upload RSA Key
Step 4: Set Permissions on – 192.168.0.11
Due to different SSH versions on servers, we need to set permissions on .ssh directory and authorized_keys file.
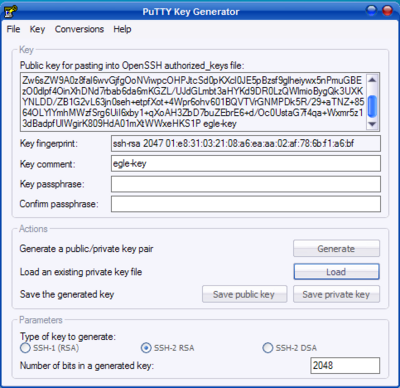
Step 5: Login from 192.168.0.12 to 192.168.0.11 Server without Password
Red Hat Generate Ssh Host Keys Download
From now onwards you can log into 192.168.0.11 as sheena user from server 192.168.0.12 as tecmint user without password.
Redhat Generate Ssh Key
SSH Remote Passwordless Login